DerSecur
Since 2011, DerSecur has led innovation in application security with its flagship product, DerScanner, providing comprehensive analysis of both source and binary code.
Our code analysis technologies were developed at the Research Institute for Fundamental and Applied Computer Science, and are now commonly used worldwide. Currently, our team comprises 70 scientists and researchers, all focused on advancing R&D solutions in SAST, DAST, and SCA analysis.
DerScanner has gained trust and appreciation in application security community:
- Recognised by Forrester among notable vendors in The Static Application Security Testing Landscape, Q2 2023 and The Software Composition Analysis Landscape Q2 2024
- Recommended by NIST
- Certified by MITRE as CWE-compatible
Secure Solutions
DerSecur offers high-quality solutions with maximum reliability and performance. Our commercial offers always consider customer needs and suggest a deep understanding of the tasks and challenges facing customers.
What We Do
We're passionate about creating great products
that help build and run secure software
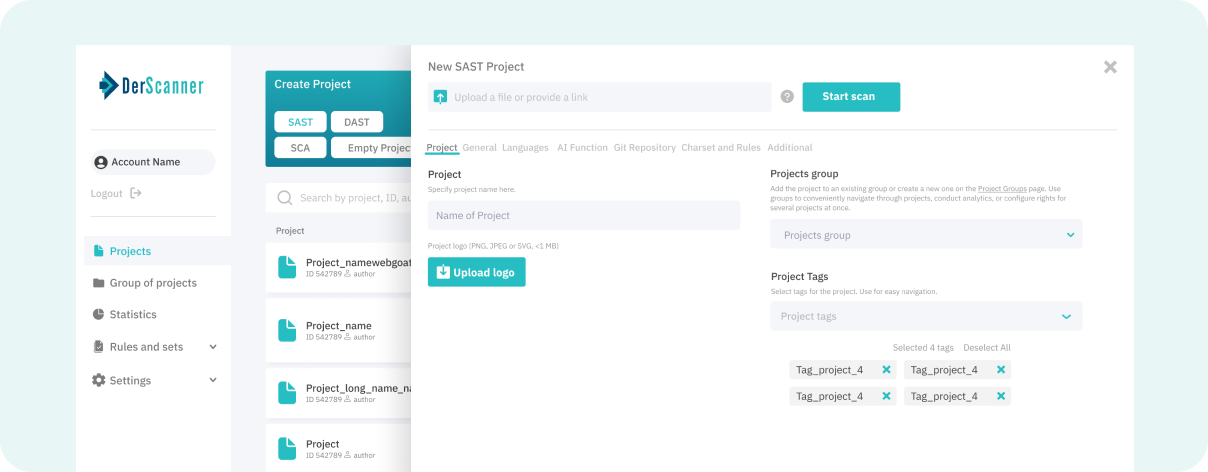
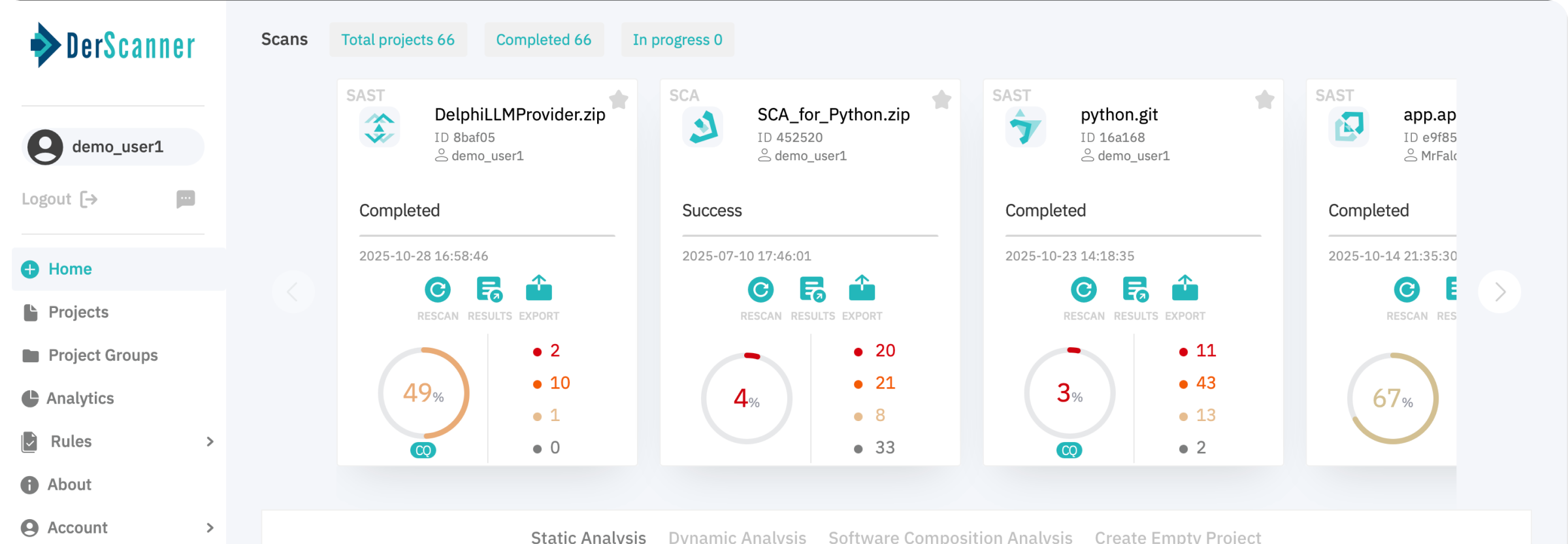
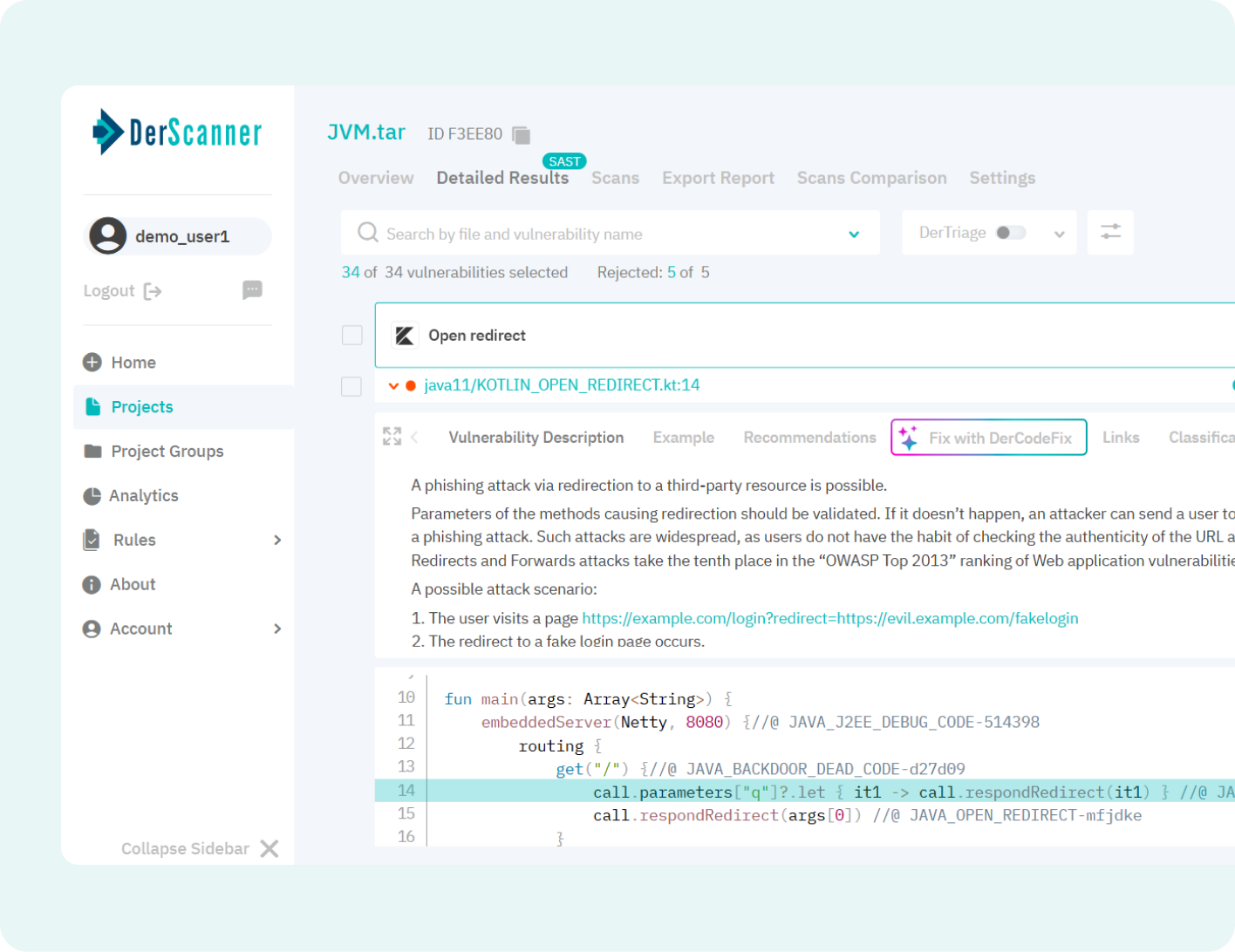
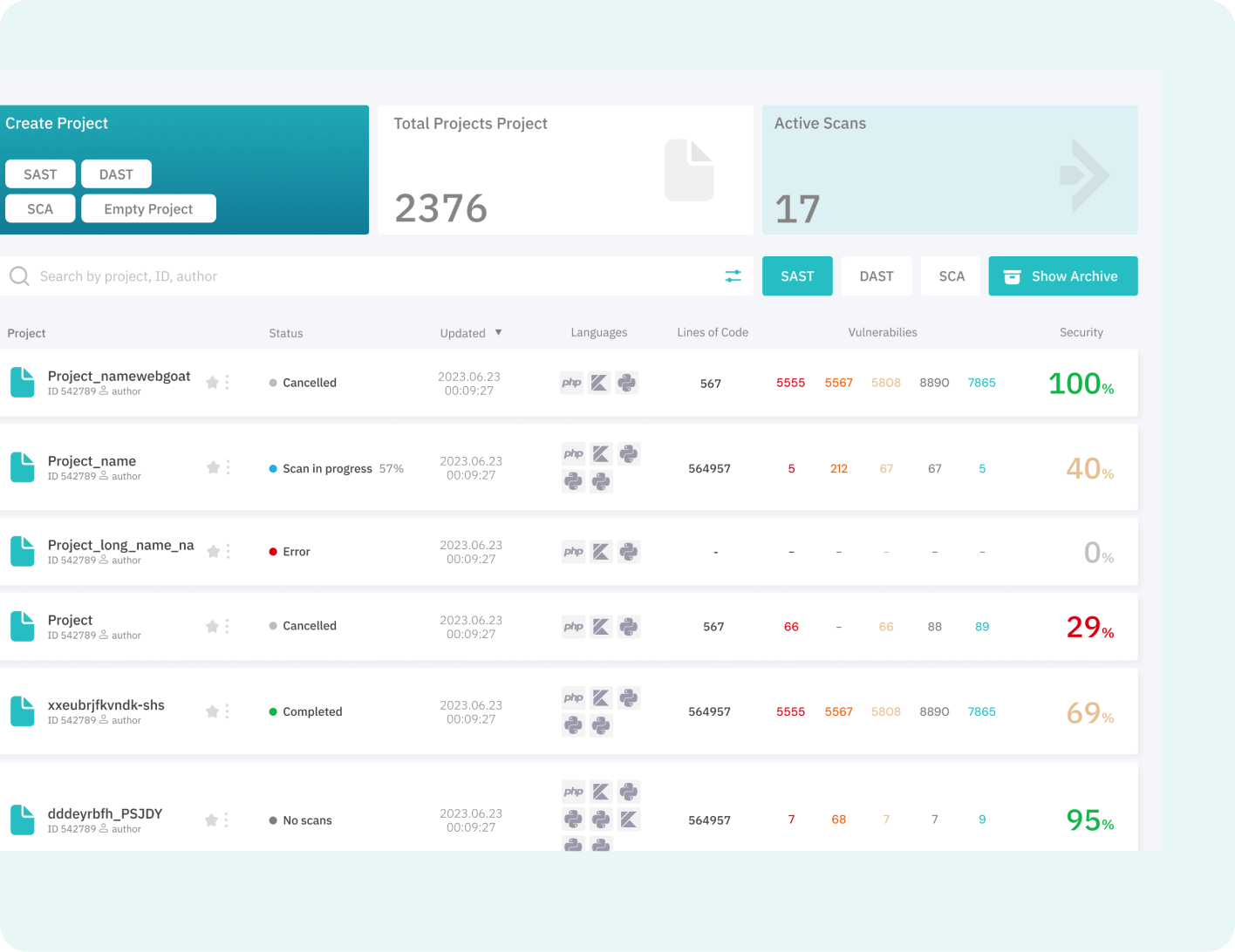
Static Application Security Testing (SAST)
Analyzes 43 languages (including legacy), ranks real risks, reduces false positives, and suggests production-ready fixes keeping your software secure
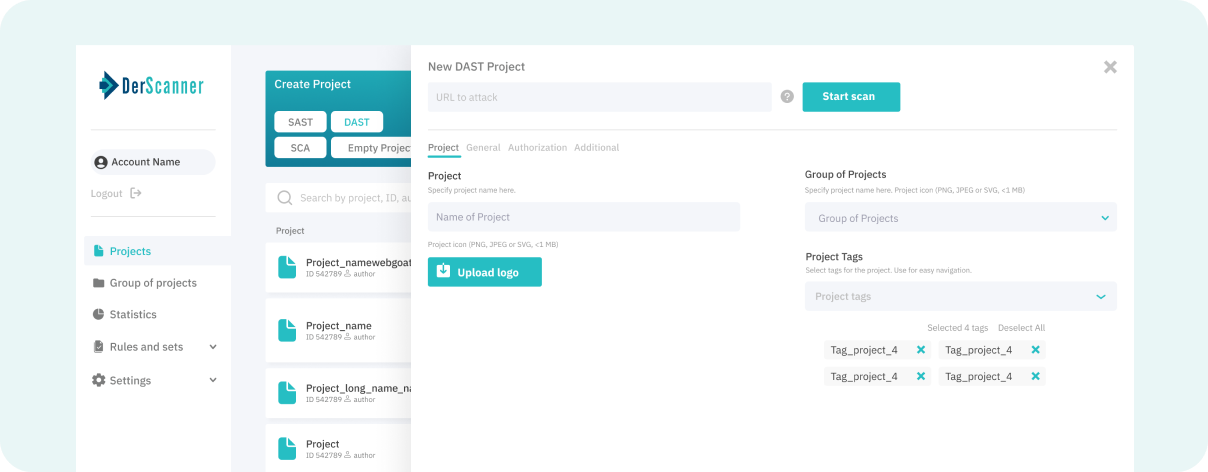
Dynamic Application Security Testing (DAST)
Exploits live applications in real time like a hacker, finds issues earlier in development and speeds up fixes.
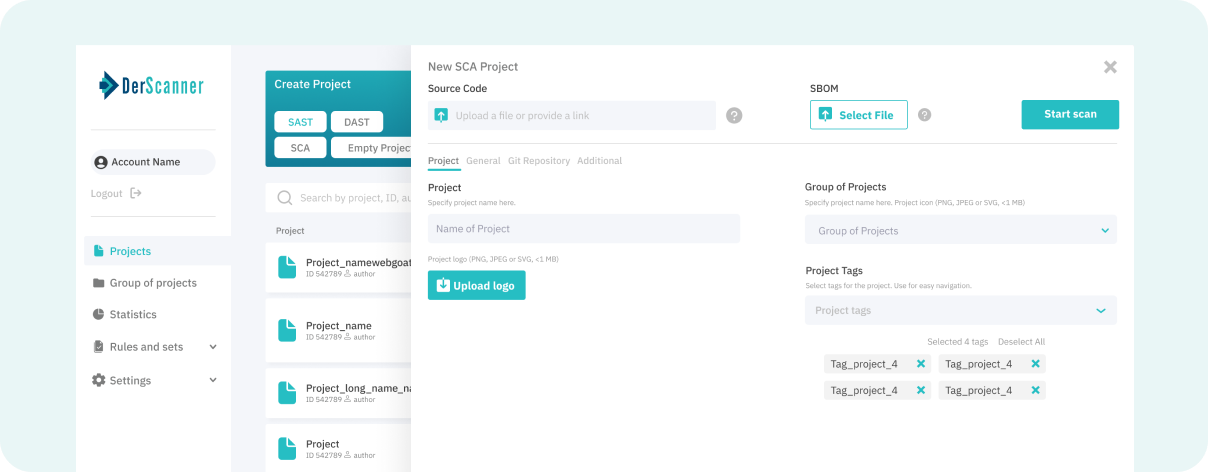
Software Composition Analysis (SCA)
Identifies all open-source components (SBOM), detects CVEs and license risks, scores package health, and prioritizes exploitable issues
Compliance
Maps findings to OWASP/CWE/PCI/HIPAA, filters by framework, and generates customizable audit-ready reports
DerSecur in lines
We’re proud of these numbers and the value we bring to application security
Trusted by






Make Your Applications
Secure Today
Sign up for a personalized demo to see
how DerScanner can meet your Application Security needs